In computer and information technology, a WORM device (write once, read many) is a type of data storage that allows data to be written to a storage medium only one time. Once it is recorded, the data cannot be erased, modified, or re-encrypted. As such, data stored on WORM storage are immutable and permanent where it can be read or accessed by users, but they cannot alter it in any way.
Write-once, Read-once files like the ones portrayed in the Mission Impossible movie and TV series: “this message will self-destruct” would not qualify as WORM data because it cannot be read by others. The same can be said for self-destructing Google GMAILs in confidential mode. The data can be deleted and erased.
Why is WORM storage important?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Storage media that support WORM capabilities are designed to be non-rewritable to prevent anyone from intentionally or accidently erasing or modifying the data after it is initially written and stored. Therefore, it provides the ability to:
-
Safeguard data integrity
-
Prevent fraud
-
Prevent evidence tampering
-
Protect data from ransomware
-
Transfer or distribute secure data offline
-
Instill trust in public records
-
Preserve data over long periods of time
Protecting data from being changed over long periods is like a business insurance policy. It not only protects data, but it protects your organization from lawsuits, regulatory compliance, malicious attacks, and ensures any high value digital assets can be reused so that economic rent can be collected from it. There are many applications and use cases across different industries and sectors. Immutable WORM storage is needed for the storage and retention of confidential data records by industries such as healthcare, financial services, legal, government departments and its agencies. The Securities and Exchange Commission requires brokers and dealers to retain their digital records on storage media that preserves the records in a non-rewritable, non-erasable format for regulatory compliance. Some states require medical patient data be preserved for over 70 years. The media and entertainment industry use WORM to archive and preserve reusable digital audio/video/animation assets. Artists, game studios, and social media companies use WORM to store and preserve all works of creation and digital property of metaverses.
Types of WORM storage
Optical storage archives and optical discs are true WORM storage through a physical and permanent change process on the medium which cannot be reversed.
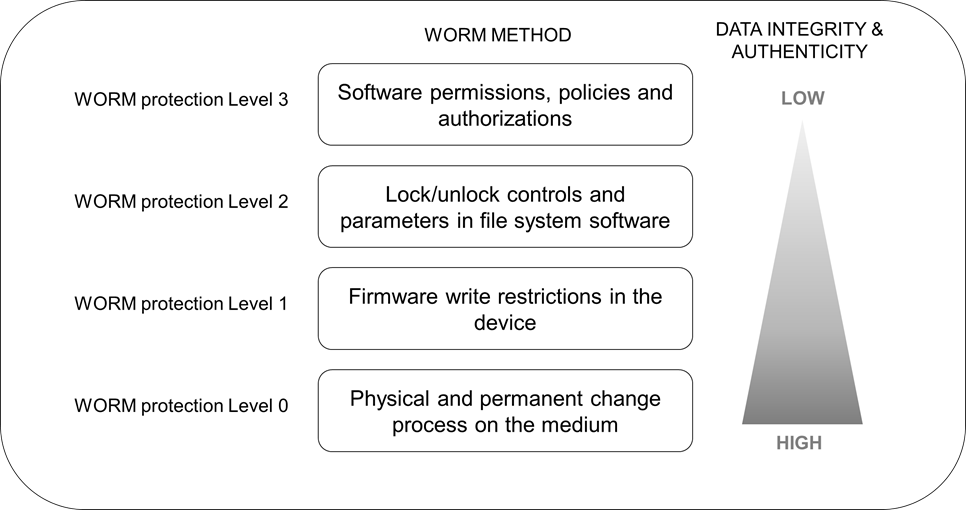
Figure 1: Immutable WORM data protection levels
Immutable storage volumes aim to protect the state of the data or file from being changed and deleted. There are several ways to achieve data immutability and WORM-like storage capabilities.
-
Use blockchain servers to write data blocks in a timestamped append-only database, interconnected by cryptography. This method only appends the record about the facts of the data, but it does not prevent the file asset from being altered.
-
Use software-based permissioned controls and authorizations to prevent data from being changed. Administrators set policies, rules and procedures that prevent users or devices from changing the data at various levels of control points. This method is highly complex and dependent on system designs and environment in which the data resides.
-
Use the file system to modify WORM configuration properties of the file directories and files to provide write protection. Administrators set parameters to lock/unlock/extend the states of the files. This method relies on the file system or the operating system to determine the status of the file and its retention periods. It assumes that users and administrators are trusted, do not have any bad intentions, and do not make any mistakes. File write protection can be changed and may rely on log files and chain of custody tracking to prove that the file has not been altered.
-
Use of firmware on hard drive or SSD flash drive to create an affect where data is locked to writeable sectors at the physical level and is embedded in the drive itself. Any used sectors cannot be allocated or rewritten a second time. The write command can be blocked at the controller level of the device by setting the device to lock.
Use inherent or built-in WORM at the hardware and medium level. This is the highest level of integrity, security, and authenticity that can be achieved because the recording surface or mechanism goes through a non-reversible physical alteration process. Regardless of any operating system or access controls that are put in place, data cannot be modified. For example, optical lasers make permanent marks on the surface of the disc and those marks are locked forever. This enables a trustless storage environment where data integrity and security that is not reliant on users, administrators, configurations, assets, or resources. No amount of administrative effort can change the contents on a true WORM storage, except via physical destruction.
Example WORM storage use cases
Professional content distribution such as financial recordings, police investigations, court testimony, electronic voting and other applications where data files must be protected from alteration or deletion – especially when data write is unlockable, moved or transferred. Organizations copy all of the data handed over to the data investigation firm onto WORM drives and one can be assured that nothing is changed after that point. Transferring a read-only file over a network with encryption and passwords does not guarantee that the file is genuine or unaltered. Also, it is always better to enforce something in hardware than software because when the software is not running, the data can be tampered with.
Corporate records
Corporate history, email, legal documents, compliance reports, contract and business transactions, audio and video libraries, intellectual property and data, training material, HR/personnel documents.
Financial and Insurance
Protect sensitive financial records, transaction history, plans, regulatory authority, SEC, SOX, Dodd-Frank Retention.
Intelligence collection
Surveillance video, dashcam, event footage from security cameras.
Law enforcement
Genuine and tamper-free police photography and audio recordings.
Electronic Voting
Ensure electronic voting records are recorded and made tamper-proof.
Court Proceedings
Secure legal files for trials, depositions, and e-discovery.
Medical Records and Devices
Retain and distribute confidential patient treatment data from medical devices such as X-rays, images, diagnostics, surgery video.
Public records
Civil records, deed records, social media, public statements and interactions with public, votes.
Artificial Intelligence
Secure offline distribution of large data sets for scientific research and machine learning.
Cyber-attack protection
Backups and archives, ransomware, air-gap protection, website protection, disgruntled employee attacks.
IT security and log files
IT security monitoring to prevent administrators from erasing or hiding their illegal activities. Sequential data, log files, security audits, IT audit trail reports, transaction meta data, access control permission logs, trace files,

